
Cloud providers are becoming a core part of IT infrastructure. Amazon Web Services (AWS), the world's biggest cloud provider, is used by millions of organizations worldwide and is commonly used to run sensitive and mission-critical workloads. This makes it critical for IT and security professionals to understand the basics of AWS security and take measures to protect their data and workloads.
As a cloud customer, it is important to understand the AWS shared responsibility model and the ten security domains you need to be aware of when using AWS. There are also actionable best practices that can improve the security of your AWS deployments.
AWS Shared Responsibility Model
The AWS shared responsibility model is a security schema that delineates the roles and responsibilities of AWS and the customer in maintaining a secure environment. Essentially, AWS ensures the security of the cloud, while the customer is responsible for security in the cloud. AWS provides a detailed diagram to clarify it:
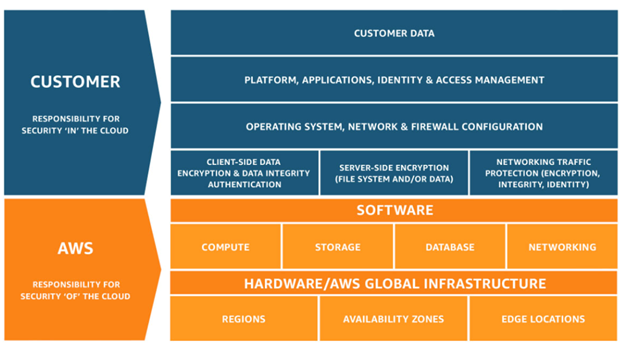
AWS Responsibilities
As part of the AWS shared responsibility model, AWS is responsible for the security and maintenance of its cloud services. This includes the physical security of its data centers and the underlying hardware and software infrastructure.
The security measures taken by AWS to protect its infrastructure include physical security controls to prevent unauthorized access to its data centers, network security measures to prevent intrusions, and system security measures to protect the underlying servers and applications. AWS also regularly updates and patches its infrastructure to protect against known vulnerabilities.
Moreover, AWS offers a range of security services and features that customers can use to secure their data and applications. These include services for identity and access management, data encryption, firewall protection, and threat detection.
Customer Responsibilities
AWS customers are responsible for securing their data, applications, and systems that they run on AWS.
Customers are responsible for managing and configuring their AWS resources to meet their specific security requirements. This includes configuring security groups and access control lists, managing Identity and Access Management (IAM) users and roles, securely configuring databases on AWS, encrypting data at rest and in transit, and implementing security best practices such as least privilege and secure coding.
Customers are also responsible for keeping their software and applications up to date, ensuring compliance with applicable laws and regulations, implementing appropriate safeguards to protect their sensitive data, and responding to any security incidents that affect their AWS resources.
Service-Specific Responsibilities
In addition to the general responsibilities outlined above, there are also service-specific responsibilities, which vary depending on the specific AWS service being used.
For example, for services like Amazon EC2 and Amazon RDS, customers are responsible for managing the guest operating system (including updates and security patches), any applications installed by the customer on the instances, and the data in transit or at rest.
On the other hand, customers have fewer security responsibilities for services like Amazon S3 and Amazon DynamoDB, where AWS operates the infrastructure layer, the operating system, and platforms. However, customers still have to manage their data (including encryption options), classify their assets, and set up identity and access management.
AWS Security Domains for Cloud Customers
Amazon's security best practices are documented in the Amazon security learning center. They are summarized in the following ten sections.
1. Data Privacy
AWS provides numerous security features and services that allow customers to protect their data effectively. For example, AWS data services like S3 provide server-side encryption to protect your data at rest, while services like AWS Certificate Manager provide SSL/TLS certificates to secure your data during transit.
In the context of data privacy as it relates to the AWS shared responsibility model, in order to ensure data privacy, customers must understand how to configure and use AWS security features correctly for each of the Amazon services they use.
2. Governance
Governance refers to the processes and policies that guide how AWS resources are used and managed. Some of the tools that AWS provides to help customers govern their AWS resources include AWS Organizations, which enables customers to centrally manage multiple AWS accounts, and AWS Service Catalog, which customers can use to create and manage catalogs of IT services that are approved for use on AWS.
Effective governance in AWS requires understanding and applying best practices. In particular, you should follow the principle of least privilege, which means granting only necessary permissions to your AWS users and encouraging accountability within the organization, ensuring that each user or department takes responsibility for securing the cloud services they use.
3. Vulnerability Management
Vulnerability management is about identifying and addressing weaknesses in your AWS environment that could be exploited to cause harm.
AWS offers several services to help customers manage vulnerabilities. For example, AWS Security Hub provides a comprehensive view of your high-priority security alerts and compliance status. AWS Inspector automatically assesses your AWS resources for vulnerabilities or deviations from best practices.
However, effective vulnerability management goes beyond using AWS services. It requires continuous monitoring, regular audits, and prompt response to identified vulnerabilities. In many cases, organizations will need to complement Amazon services with third-party vulnerability assessment tools.
4. User Device Management
User device management involves managing the devices used to access AWS. Amazon has a few services that help manage user devices. For example, AWS WorkSpaces provides a secure, cloud-based virtual desktop experience that employees can access from anywhere.
To manage user devices effectively, you must implement strong device security policies, such as requiring device encryption and strong passwords. You should also use Multi-Factor Authentication (MFA) for added security. It is critical to ensure that all devices accessing your AWS resources have operating system patches applied and malware protection.
5. Risk Management
Risk management in AWS encompasses the identification, assessment, and mitigation of risks associated with your AWS usage.
The AWS Risk and Compliance Program provides information about AWS's approach to risk management. AWS Trusted Advisor provides real-time guidance to help you provision your resources following AWS best practices.
Effective risk management requires a proactive approach, including regular risk assessments and implementing risk mitigation measures.
6. Network Management
Network management entails managing your AWS network infrastructure, including your VPCs, subnets, route tables, and network gateways.
AWS presents several services to help with network management, such as Amazon VPC for creating isolated virtual networks and AWS Direct Connect for establishing a dedicated network connection from your premises to AWS.
Effective network management requires understanding AWS networking concepts and following AWS best practices. For instance, you should use security groups and network access control lists (ACLs) to control inbound and outbound traffic to your machine instances.
7. Managing Identity & Access
Managing identity and access includes controlling who can access your AWS resources and what they can do with them.
AWS furnishes the AWS Identity and Access Management service for this purpose. IAM allows you to manage users, groups, roles, and permissions in AWS. To manage identity and access effectively, you should follow the principle of least privilege, regularly review and update your IAM policies, and use MFA for added security.
8. Incident Response
AWS provides several tools to help with incident response, such as AWS CloudTrail for logging and monitoring activity in your AWS account and AWS CloudWatch for collecting and tracking metrics about your AWS resources.
Effective incident response requires creating an incident response plan, training your team to execute the plan, and regularly testing and updating the plan.
9. Configuration Management
Several AWS tools are available to assist with configuration management, such as AWS Config for tracking resource configuration changes and AWS Systems Manager for gaining operational insights and taking action on your AWS resources.
Effective configuration management requires understanding AWS configuration options and following best practices. Administrators must learn and apply secure configurations to each service and resource running in AWS and take measures to avoid the removal of secure configurations, whether accidental or malicious.
10. Business Continuity
Business continuity planning ensures that your business can continue to operate even in the face of disruptions or disasters. Some of the AWS offerings to help with this endeavor include AWS Backup, which manages backups across all Amazon services, and Amazon CloudFormation, which can help automatically redeploy complex systems to the cloud after a disaster.
To ensure business continuity, you should have a well-planned and regularly tested disaster recovery plan. You should also leverage AWS's global infrastructure to build redundancy into your applications and data storage. Amazon lets you deploy almost every resource across multiple availability zones (AZs representing different data centers) or even across different geographical regions.
7 AWS Security Best Practices
Some critical best practices can help you improve the security of your Amazon environment:
1. Use the AWS Well-Architected Framework
The AWS Well-Architected Framework is a guide for building secure, high-performing, resilient, and efficient infrastructure for your applications. It provides architectural best practices across five pillars: Operational Excellence, Security, Reliability, Performance Efficiency, and Cost Optimization.
The Security pillar emphasizes the importance of protecting information and systems and offers critical practices for ensuring confidentiality and integrity of data, identifying and managing who can administer privilege management, protecting systems, and establishing controls to detect security events.
2. Maintain a Consistent Security Posture Throughout AWS Deployments
A consistent security posture demands the application of the same security measures and standards across all your AWS deployments. This includes consistently configuring security groups, maintaining uniform IAM policies, and regularly auditing your environment for any deviations. AWS Security Hub can help maintain this consistency by aggregating, organizing, and prioritizing your security alerts and findings from multiple AWS services.
3. Apply the Principle of Least Privilege
The principle of least privilege is a cybersecurity concept where individuals are given the minimum levels of access necessary to fulfill their job functions. This approach reduces the risk of unauthorized access and data breaches. In AWS, the least privilege principle can be implemented using IAM policies. By creating custom policies for each role in your organization, you can ensure that each user has access only to the resources they need.
4. Regularly Rotate and Secure Access Keys
Access keys in AWS consist of a pair: an access key ID and a secret access key. These keys are used to sign programmatic requests that you make to AWS if you use AWS CLI, AWS SDK, or direct HTTP calls.
Rotating access keys means that you're actively changing them, preventing any unauthorized users from gaining prolonged access. It's good practice to change your access keys every 60 to 90 days.
When replacing keys, remember to secure them properly. Never embed access keys directly into your code. Instead, use AWS Identity and Access Management (IAM) roles. If you need to share access keys, use AWS Secrets Manager.
5. Patch EC2 Instances Regularly
Amazon Elastic Compute Cloud (Amazon EC2) provides scalable computing capacity in the AWS cloud. Keeping your EC2 instances up to date is crucial for securing your data.
Regular patch management of your EC2 instances can help protect your data from the latest security threats. Services such as AWS Systems Manager Patch Manager can automate the process of patching managed instances.
6. Use Versioning in S3
Amazon S3 is Amazon's elastic object storage service. One of its key features is bucket versioning, which allows you to preserve, retrieve, and restore every version of every object in your bucket. By enabling versioning, you can recover from both unintended user actions and application failures. It also adds an extra layer of protection against malicious attacks, as you can easily revert to a previous version of your data.
7. Carry Out Code Reviews
In addition to infrastructure security, AWS also advises secure code practices. Code reviews involve systematically checking your team's code for errors, vulnerabilities, and deviations from coding standards. In the context of AWS, code reviews can help identify security issues like hard-coded credentials or unsecured API endpoints. AWS CodeReview is a service that makes this process easier by providing automated code reviews for your AWS applications.
Conclusion
Understanding and implementing AWS security is fundamental for any organization leveraging Amazon's cloud services. The AWS shared responsibility model emphasizes the distinction between AWS's role in securing the cloud infrastructure and the customer's duty to secure their data and applications within the cloud. The ten essential security domains, ranging from data privacy and governance to incident response and business continuity, are all parts of a solid understanding of cloud security. Each domain presents unique challenges and opportunities for securing your AWS environment.
Implementation of the seven AWS security best practices will strengthen your cloud security posture. By understanding and applying these principles and best practices, organizations can significantly enhance the security of their AWS deployments. Ultimately, the responsibility to secure your AWS environment rests with you, and through diligent application of these strategies, you can achieve a secure, resilient cloud environment.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor and do not necessarily reflect those of Tripwire.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

