This piece was originally published on Fortra’s AlertLogic.com Blog.
Thinking about your own network isn’t enough to keep your business safe and profitable. As more buyers, sellers, and partners collaborate ever more closely across the world, supply chain IT risks are rising with no slowdown in sight. According to the Identity Theft Resource Center, supply chain attacks surpassed malware incidents by 40% in 2022.1 There’s never been more at risk for wide collections of companies that depend on each other.
According to Josh Davies, Fortra’s Alert Logic Principal Technical Product Marketing Manager, “Supply chain hacks are some of the most dangerous and complicated threats we see in cyberspace today.” It’s therefore crucial to understand how they occur and what your risk is, because there’s so much more to think about when it comes to the security of the vendors and partners you’re relying on. Davies tackled this topic recently in a special webinar on supply chain compromise — part of our Cybersecurity Summit — focusing on the dangers and solutions to have ready to meet them.
How Does a Supply Chain Compromise Happen?
Davies says that, essentially, we can boil these assaults down to “a trusted delivery mechanism” that trickles one successful breach through the chain to many more victims. With a single point of entry, a nefarious web actor can infect many networks in disparate locations. So, how do they accomplish it?
Websites
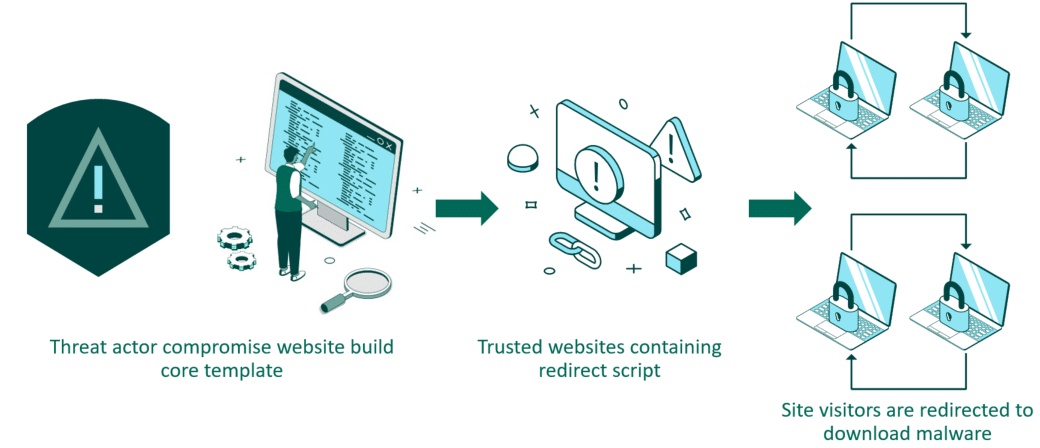
Websites are a prime delivery mechanism for supply chain compromise, as numerous users from any location will frequently visit sites they trust. Threat actors could compromise a core template in a website’s build agency, hiding malicious code there. A redirect script then is deployed to make users download malware or direct them to another high-risk site. Anyone who uses that website, Davies explains, “is inadvertently going to compromise themselves.”
Website Builder Compromise Process
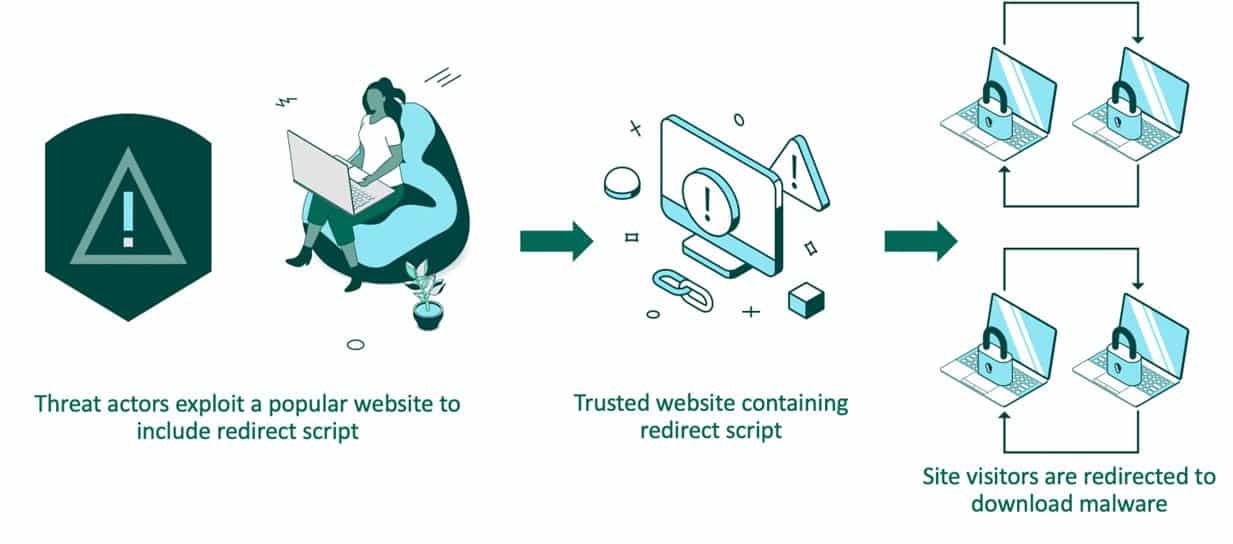
We commonly see “watering hole” attacks — the pinnacle of mass infiltration. Watering hole tactics infect a web application with a high visitor count, or in a targeted example, a website with a certain user profile that is attractive to the adversary. “This one is slightly different to the website builder compromise” Davies adds, “as it’s not trying to compromise the code that somebody uses, or something in the build process. Instead, it’s a live application or website and hackers exploit it directly. They might know it’s going to have a lot of visitors — like a banking site.” You poison the watering hole that everyone usually drinks at, they turn up the next day, suspecting nothing, drink the water and leave poisoned. This is exactly how the attack works, the trusted website prompts you to download something, you think nothing of it as you’ve been here a thousand times, but you download malware. This download technique is often called a drive-by.
Watering Hole Attack Process
Drive-by
Automatic downloads of malware, like a remote-access trojan (RAT) tracking movements and data of the compromised user, like passwords or credit card info they type. Since the download request tends to come from a trusted website — or an imposter site that a cybercriminal has set up, mimicking legit sites — the user might be unaware of what’s happening.
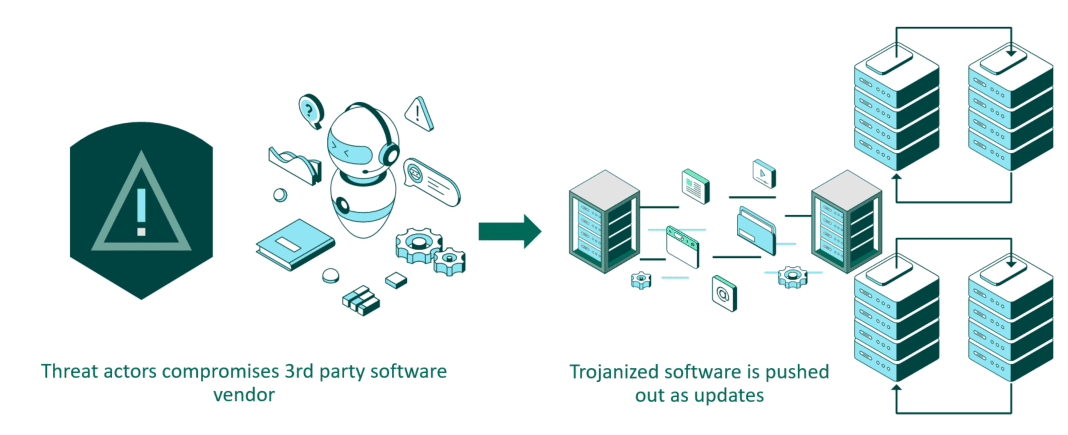
Third-party software
If someone compromises a software developer, they can embed their own code into newer versions of the software. Backdoors then are shipped in regular software updates within code that isn’t heavily scrutinized. Davies reminds us that, “Nothing’s going to block them. They’re code-signed. They look, feel, and smell like legitimate activity. You update your software all the time and no one has time to review every line of code”. The famous SolarWinds supply chain compromise is a prime example.
Third-Party Software Compromise Process
Third-party hardware
Tiny chips can be added to hardware introducing a backdoor. These chips can be as small as half the size of a pencil head, are difficult to spot and in diversified manufacturing chains can introduce compromise into the final product. Some vendors, like Huawei, have been prohibited by certain governments from being included in critical infrastructure, because of the perceived risk of foreign governments being able to use their hardware for subterfuge or cyberattacks.
Extending Supply Chain Risks to Mergers and Acquisitions
Davies is firm on one point above all: “There’s no such thing as a silver bullet in security.” That’s why you need to prepare for post-compromise situations. Containing and disrupting the attack sequence is crucial to getting back on your feet as quickly as possible, limiting the spread from business-critical systems or data. This requires the visibility and knowhow to holistically understand and address a compromise, so as to prevent reinfection due to inconclusive remediation.
At Fortra’s Alert Logic, we’ve learned over many years that a merger and acquisition (M&A) is a particularly risky time for companies that must gauge new security risks when combining people, data, and networks. Our managed detection and response (MDR) solution is primed to show where weaknesses may exist before organizations align, while also alerting on active compromises with 24/7 SOC monitoring.
M&A Compromise Timeline Example
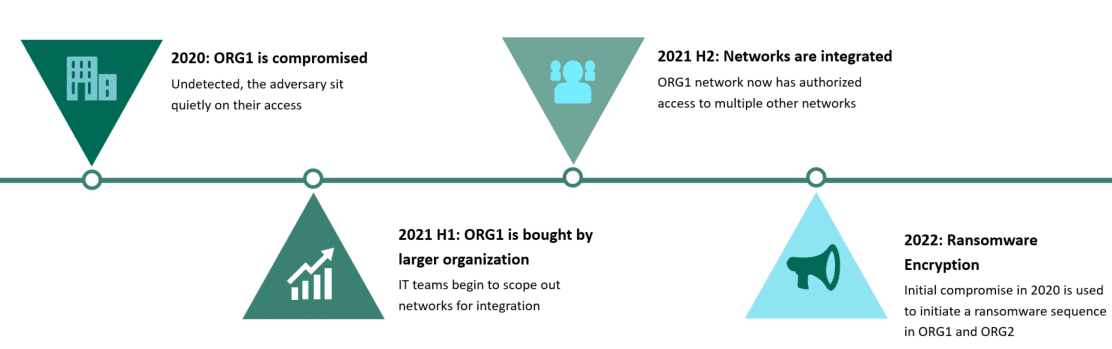
Our Threat Risk Index reports and dashboard breaks down risks across your cloud/on-premises/hybrid environment, presenting a handy risk “score” which can be matched with business context and risk appetites. You can assess specific networks before deciding whether you want to integrate them within a wider network. This is useful for M&A because smaller networks can carry a high vulnerability score that could introduce compromises when fully integrated. How long has it been exposed? Could an attacker have compromised it already? We aim to answer such questions prior to the merger.
“The difference,” Davies explains, “is that supply chain compromises are usually done with the intention of moving on downstream. Mergers and acquisitions are a bit trickier to gauge. If you know that Organization One is going to buy Organization Two in a year, you’re probably better off using that information to bet on the stock market instead.” However, joining the networks together creates a trusted delivery mechanism typical of supply chain compromise, even if the outcome is more coincidental than deliberate.
Our Threat Risk Index, however, shows risks across cloud, on-premises, and hybrid networks. If you do want to thoroughly analyze cybersecurity risks in M&A, you’ll gain far more peace of mind, especially when acquiring other companies. “We can also prioritize exposures — for example, if they’re internet-facing, there is an increased chance of compromise, so we’ll assign a much higher priority to it. Then we’ll give you a breakdown comparing the networks side by side.”
Real World Example of Supply Chain Compromise
SolarWinds Orion Under the Microscope
Davies’ discussion brought up a significant case study that highlights what can go wrong with a supply chain compromise and how a security solution can make sense of complex attack vectors, mitigating damage wherever possible.
Before spring 2020, SolarWinds was riding high on business and government contracts worth hundreds of millions of dollars. Its Orion software scales, manages, and monitors infrastructure for consolidated IT administration. At the time, 33,000 organizations used Orion for essential operational functions. Yet, once attackers managed to compromise a SolarWinds’ Microsoft 365 account in 2019, they began preparing one of the most severe cyber assaults in recent memory. They inserted their own code into a software update, known as the “SunBurst” backdoor, shipped it alongside the official patch infecting 18,000 organizations when they updated their software. By compromising one organization and using that access intelligently, they now had access to 18,000 organizations.
SolarWinds Orion Supply Chain Compromise Timeline
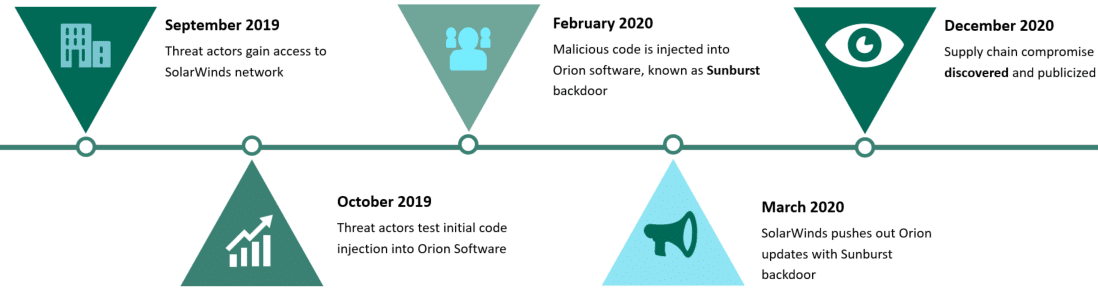
As Davies describes it, these state-linked threat actors were about “the low-and-slow game,” quietly gathering data on multinational and federal groups. Out of 18,000 attack opportunities, they chose to target around 50: organizations such as FireEye, Department of Homeland Security, and the U.S. Treasury.
When the attack hit, several Orion users were fortunate to have Alert Logic for defense and a root-cause investigation. Our 24/7 human-led protection gave our customers rapid insight into how breaches on the application could affect them. “The one thing you must ensure you have,” Davies says, “is all the relevant data in your environment, so when something like this happens, you can connect the dots as best you can.” Inside threat techniques, for instance, revealed lateral movements and command-and-control actions. We could trace the breach and report on exactly what was at risk, how many systems they’d pivoted to, which data may have been accessed. From there, it was a matter of suggesting which systems to cordon off or restore from backups, as well as providing insight into the initial entry vector, the Orion SolarWinds patch. Supply chain compromise is a perfect example for needing to spread your detections across attack chains, as the entry vector was near impossible to detect when it occurred, but detecting the next steps of compromise let us know something was wrong so we could get expert eyes to scrutinize the data further.
But that’s just one case of what we can uncover and suggest at any stage of an attack, limiting the fallout from exponential supply chain weaknesses. Want to find out more about Fortra’s Alert Logic MDR? Speak to an expert, request a demo, or watch our 2022 Cybersecurity Summit for a closer eye on the assets, networks, and users that keep you competitive.
Zero Trust and the Seven Tenets
Understand the principles of Zero Trust in cybersecurity with Tripwire's detailed guide. Ideal for both newcomers and seasoned professionals, this resource provides a practical pathway to implementing Zero Trust, enhancing your organization's security posture in the ever-evolving digital landscape.